Cyber Security measures are taken to safeguard computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks, illegal access, and improper use.
Reasons Why:

When you lack knowledge about cyber threats and best practices, it opens the door for cybercriminals to infiltrate your network’s and computers. They can steal sensitive information and cause significant financial and reputational damage.
Security is a team sport, it’s not just the responsibility of security and IT pros but requires everyone to understand the risks and how to avoid pitfalls.
Email is widely used in business communication because of its organizational benefits, accessibility, authenticity, and privacy advantages. Criminals use Spear Phishing, Ransomware, Spoofing, Spam Scams, Social Engineering and Malware.
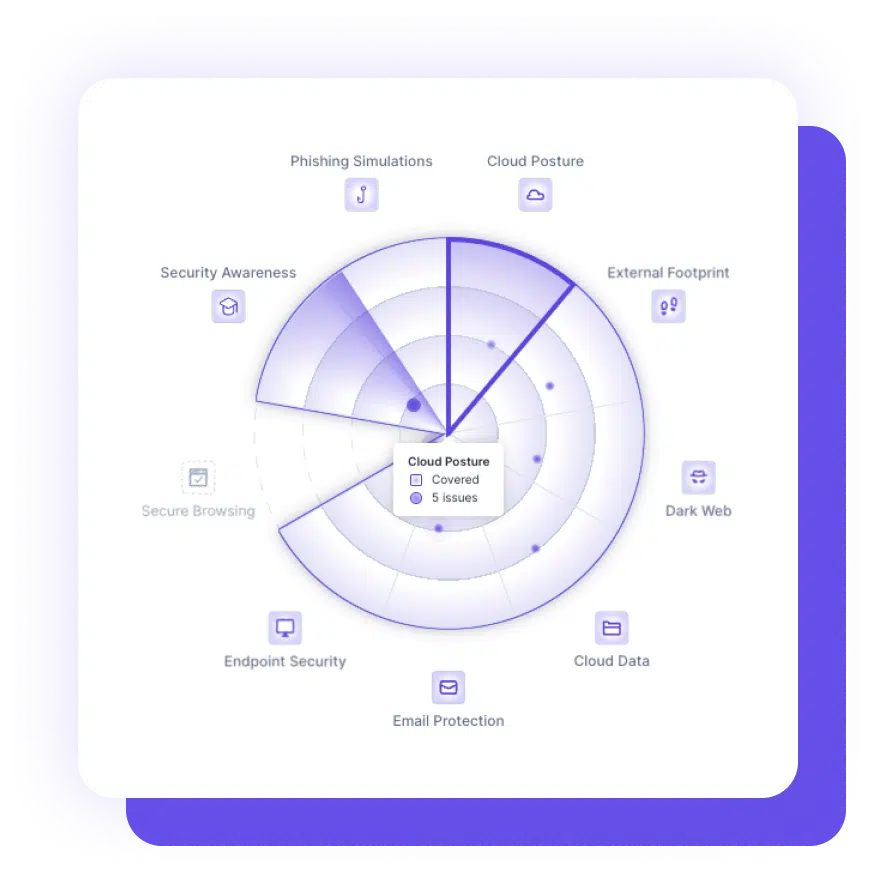
As more and more businesses are shifting to cloud-based applications, cybercriminals are also adapting their tactics to exploit the vulnerabilities that exist in these environments. Data exposures include: Data Exposure, Misconfiguration, Third Party Risks, Inactive Users, Excessive Permissions and Targeted Attacks.
Businesses face high levels of footprint from external threats posed by the dark web and other forms of external exposure. Cybercriminals can exploit vulnerabilities at any moment to cause data breaches, financial losses, and reputational damage. You nee to be aware of: Exposed Services, Missing Records, Invalid Chains of Trust, Leaked Credentials, Evilving Ecosystems and Business Targeting.
A device threat can compromise the security of an electronic device and lead to negative consequences such as data breaches, financial losses, or identity theft. These threats are: File& Fileless Malware, Ransomware, Spyware& Keyloggers, Advanced Threats, Trojan Horses, Botnets, Adware & PUPs.
Email is widely used in business communication because of its organizational benefits, accessibility, authenticity, and privacy advantages. Nonetheless, its popularity also makes it an appealing target for cyber criminals. Exploits include: Email Phishing, Social Engineering, Whaling, Employee Negligence, Malicious Downloads and Operational Damage.
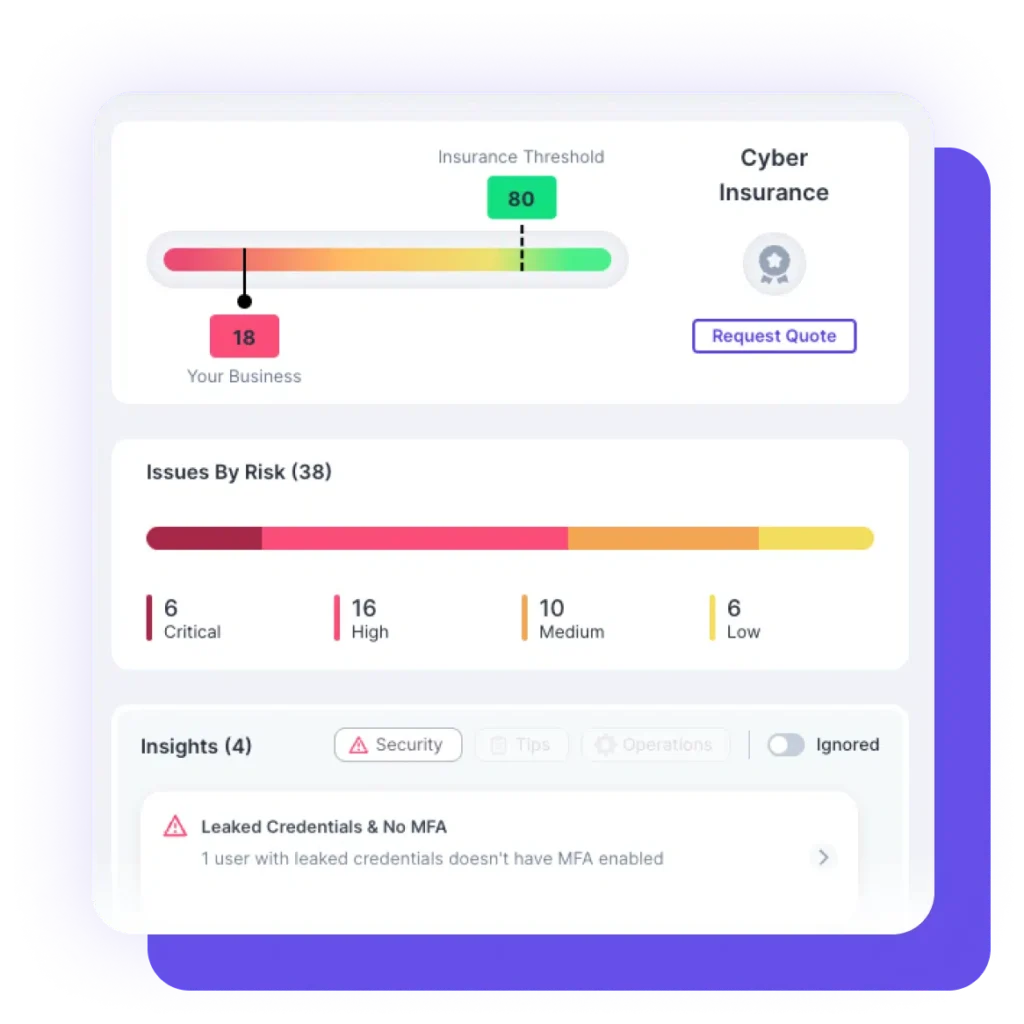
In data loss scenarios, paying a ransom provides no guarantee that the hackers will return the data uncorrupted or at all. There’s always a risk of permanent information loss. Losses include Financial loss, Business Disruption and legal Cost and most importantly Loss of Credibility and Trust.
85% of data breaches
were due to the “human mistakes”
Taking a comprehensive approach to cybersecurity. Our holistic protection encompasses all layers of defense, providing a unified shield against threats and vulnerabilities, ensuring your organization’s security is robust and thorough.
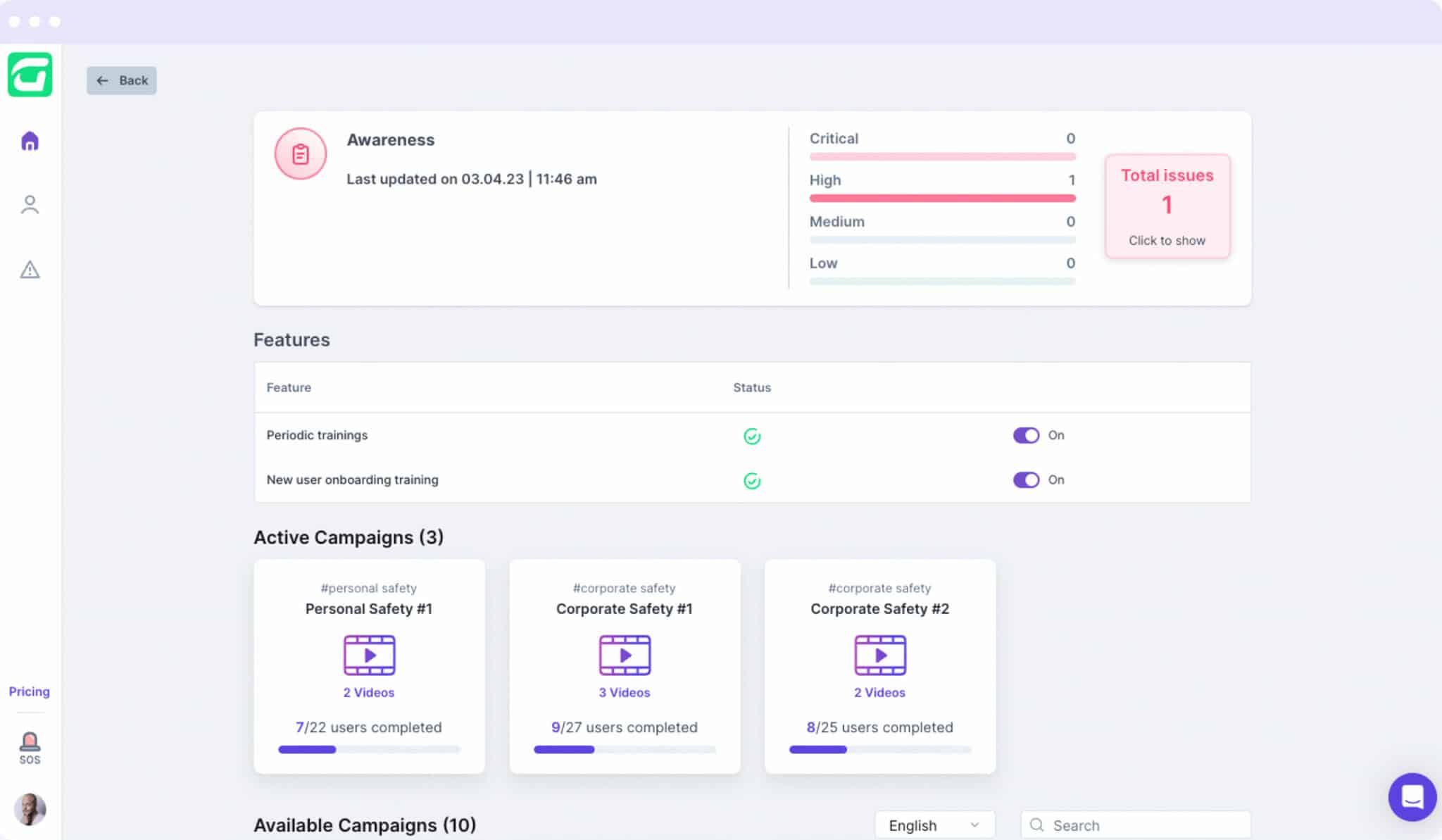
When it comes to managing multiple clients, it can be overwhelming to address every potential threat. CTS Cyber Threat Security enables you to seamlessly oversee and navigate your portfolio of clients’ threats from the start, saving you time.
Centrally navigate the security of multiple clients, each with their unique environments and potential attack vectors, from a single platform, ensuring efficiency, better visibility, and consistency when securing your clients’ systems and data.
With one-click remediation and powerful integrations, even non-security experts can swiftly respond to cyber events.


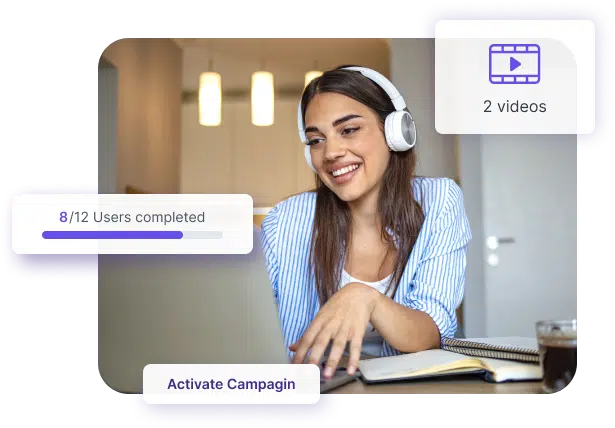
Implementing security helps to ensure that all members of your business are knowledgeable about potential security threats and how they may manifest. This type of team awareness fosters a security-focused culture and motivates individuals to adhere to best practices.
At CTS Cyber Threat Security, we recommend conducting awareness training on a weekly, or monthly basis to keep employees informed and up to date on the latest cybersecurity threats and best practices.
The benefits of cyber security includes increased employee awareness of cyber threats, improved employee security practices, reduction in security incidents, and protection against data breaches.
The effectiveness of security can be measured through various methods, identifying maliciuos behavior, remediating problems and maintaing security incident reports. Our platform uses AI and engineers to effectively manage cyber actions and keep your computers and networks in top performing conditions.
Yes, an employee cyber awareness campaign can be customized to fit the specific needs and risks of an organization. For example, a healthcare organization may need to emphasize the importance of patient data privacy, while a financial institution may need to focus on phishing attacks targeting financial data.

