Strengthen your digital perimeters and eliminate external exposures by implementing effective security from the outside in.
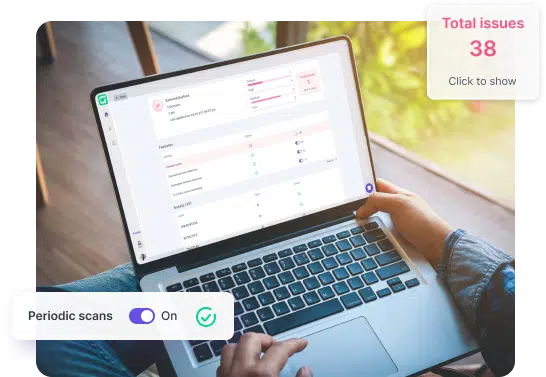


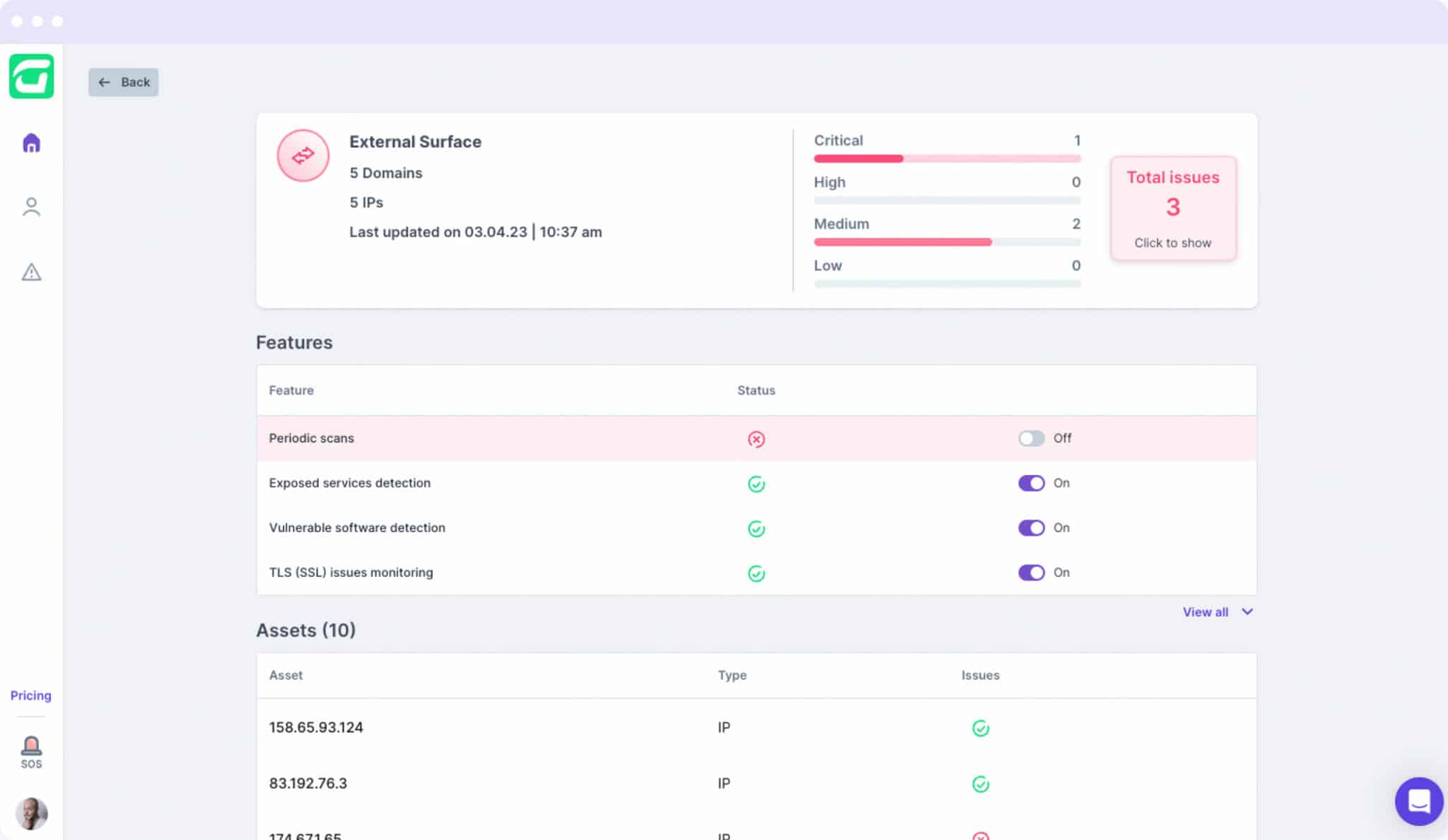
With an innovative solution and multi-layered approach, CTS Cyber Threat Security begins with an External Footprint assessment and deep analysis of how a threat actor would view a business’s external posture. Rest assured that employees’ and clients’ digital assets are not exposed and are continuously monitored for vulnerabilities.
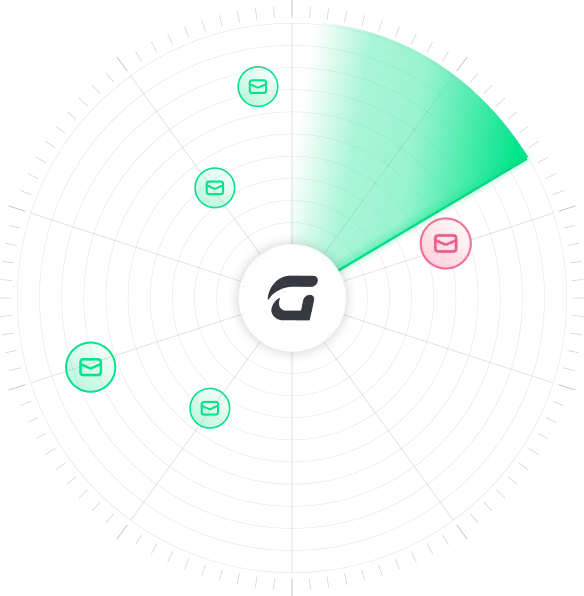
Businesses face high levels of footprint from external threats posed by the dark web and other forms of external exposure. Cybercriminals can exploit vulnerabilities at any moment to cause data breaches, financial losses, and reputational damage.
Incorrect DNS records, missing SPF or DKIM records, and other configuration errors can lead to phishing attacks, spoofing, and other targeted email-based cybercrime.
Leaked credentials are typically found in data dumps and other lists on the dark web and pose a critical risk to employees and businesses if they go unchecked.
65% of spear phishing attacks originate
from leaked credentials purchased on the dark web
65% of spear phishing attacks originate
from leaked credentials purchased on the dark web
CTS Cyber Threat Security scans for open ports and public exposures to prevent malicious actors from accessing vulnerable and outdated services.
Discovering the current use of protocols in public domains and servers enables CTS Cyber Threat Security protocol monitoring for missing TLS/ SSL certificates.
CTS Cyber Threat Security continuously monitors the internet for leaked credentials and exfiltrated data, triggering alarm bells when the keys to the castle are in nefarious hands.
Using machine learning tools, CTS Cyber Threat Security scrapes and analyzes dozens of sources that monitor the dark web for malicious activity targeting businesses and users.
After signing up with a business domain, Guardz initiates an initial risk assessment.
CTS remediation playbooks enable precise steps for simplified resolution, leveraging industry best practices.
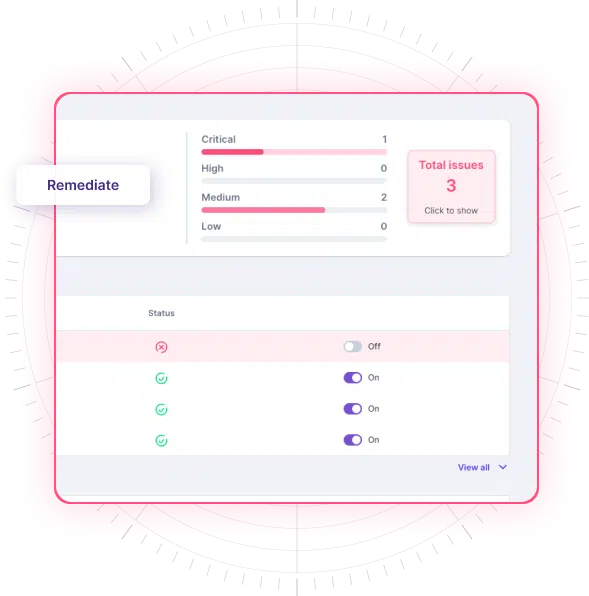

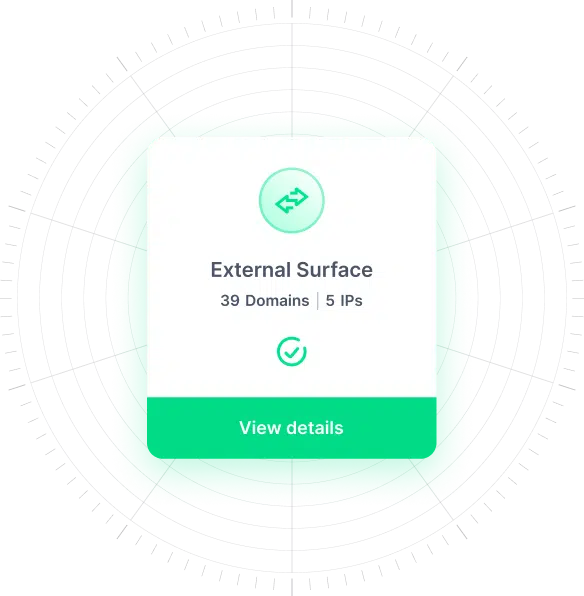
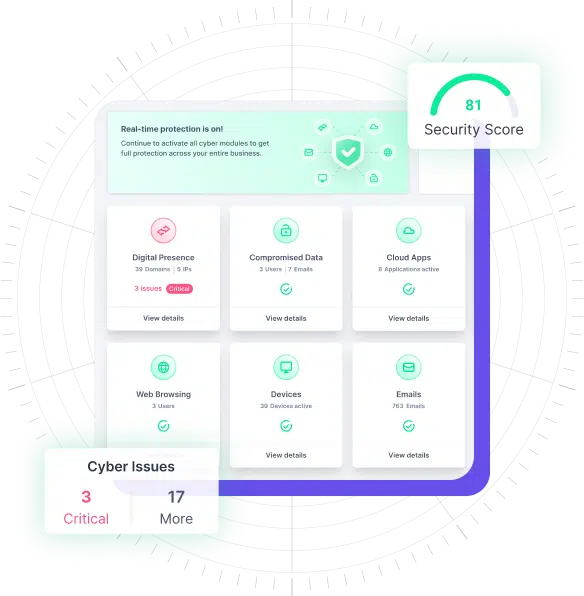
Centrally navigate the security of multiple clients, each with their unique environments and potential attack vectors, from a single platform, ensuring efficiency, better visibility, and consistency when securing your clients’ systems and data.
With one-click remediation and powerful integrations, even non-security experts can swiftly respond to cyber events.
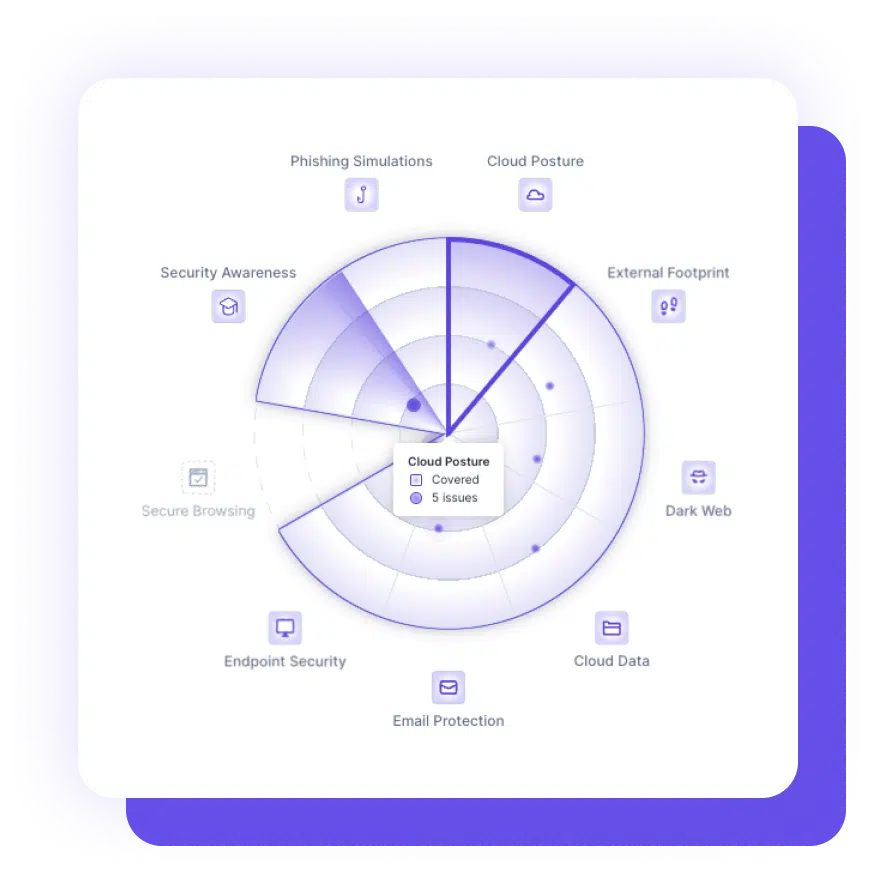


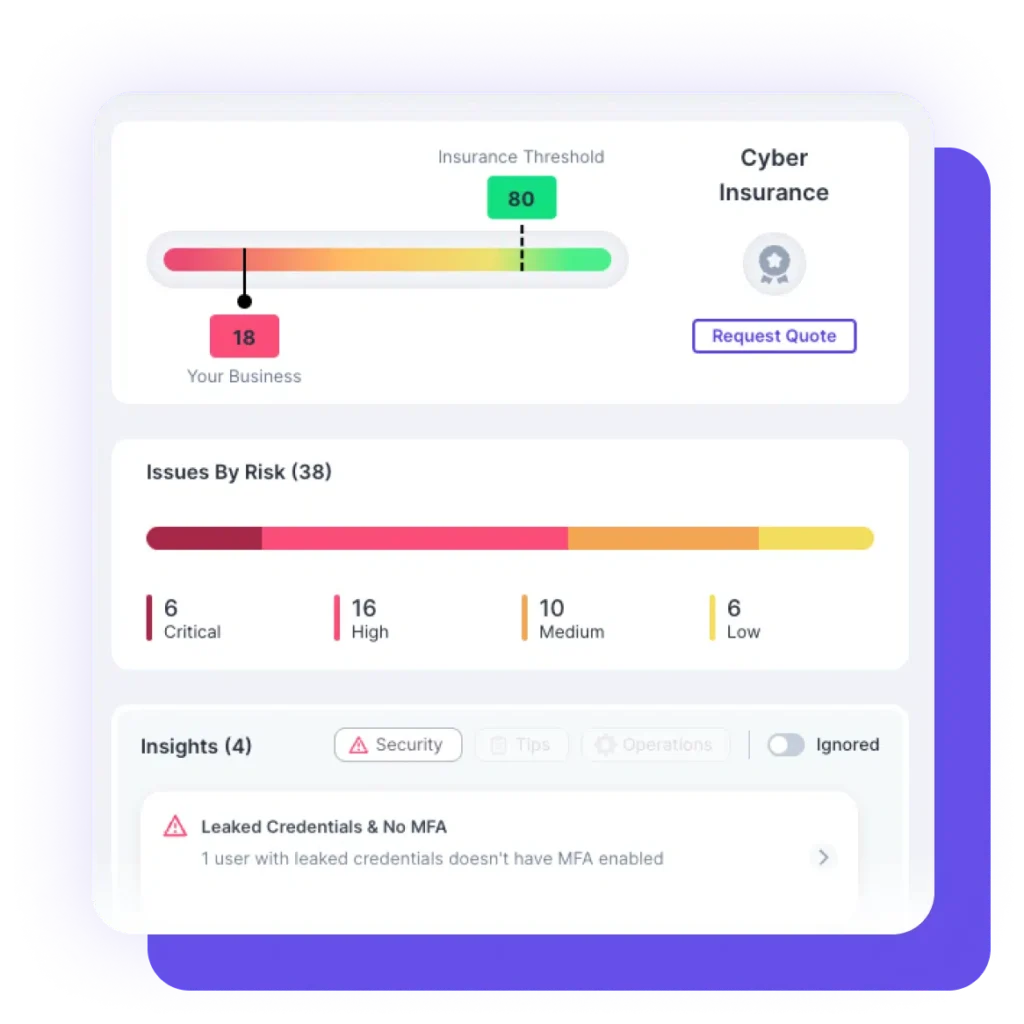
Third-party vendors may introduce new footprints to your business, as they may have access to your systems and networks or be responsible for handling sensitive data. It is important to carefully vet and monitor third-party vendors and contractors to ensure they meet your security standards and do not introduce new vulnerabilities.

