Discover end-point threats in real-time to prevent issue escalation and automate remediations when it matters.



With an innovative solution and multi-layered approach, CTS Cyber Threat Security ensures that company-managed devices are fully protected and monitored from malicious threats.
Rest assured that employees and clients’ can focus on their day-to-day business while their devices are actively secured by industry-leading end-point security.

Malware downloaded from email attachments or websites, also embedded in legitimate software, damages computers and servers.
Lack of education regarding how hackers and cyber criminals target individuals leaves employees vulnerable to clicking a link without realizing the impact.
70% of successful breaches
begin on endpoint devices.
CTS Cyber Threat Security detects outdated operating systems and vulnerable software so you can take appropriate actions with the guidance of the CTS Cyber Threat Security playbooks.
Leverage CTS Cyber Threat Security on top of the native anti-virus and anti-malware capabilities to manage and protect endpoints with automated remediations.
Working hand-in-hand with the CTS Cyber Threat Security browser extension, ensure employees are not exposed to malicious sites, web redirects, unsafe extensions, and more during their day-to-day internet activity.
By monitoring device processes and executables across an organization, CTS Cyber Threat Security can assist with investigation and response as threats are identified and for post-incident attack-chain analysis.
The CTS Cyber Threat Security device agent continuously monitors activity on designated end points, integrating with existing AV tools and communicating status to the management system.
Designed to identify anomalies in executables, processes, autoruns, and command-level activity, the CTS agent surfaces the information that matters with an urgency that reflects the relevant risk.
Using the combined intelligence of the CTS threat operations team and machine learning tools, malicious activity is isolated from the noise and brought to the forefront.
CTS delivers the relevant alerts and insights to system admins through issues and alerts to enable timely responses and communication with the relevant parties.
The CTS remediation options vary according to the findings but empower admins to implement automated resolutions or follow detailed playbooks to solve the issues manually.



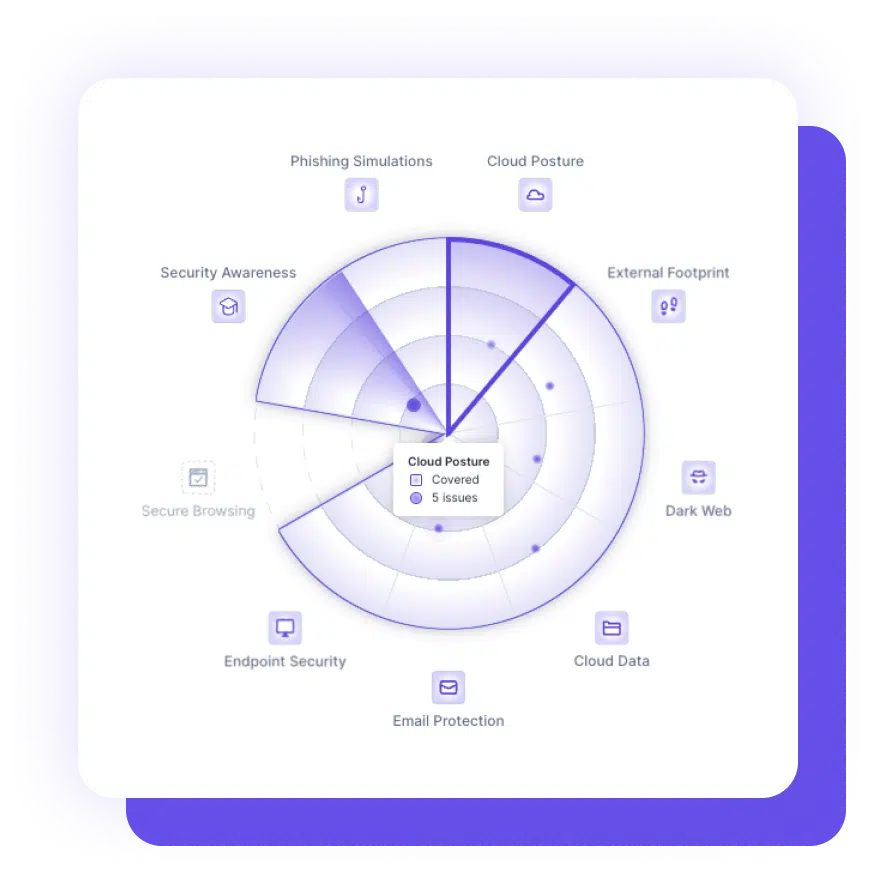
Centrally navigate the security of multiple clients, each with their unique environments and potential attack vectors, from a single platform, ensuring efficiency, better visibility, and consistency when securing your clients’ systems and data.
With one-click remediation and powerful integrations, even non-security experts can swiftly respond to cyber events.


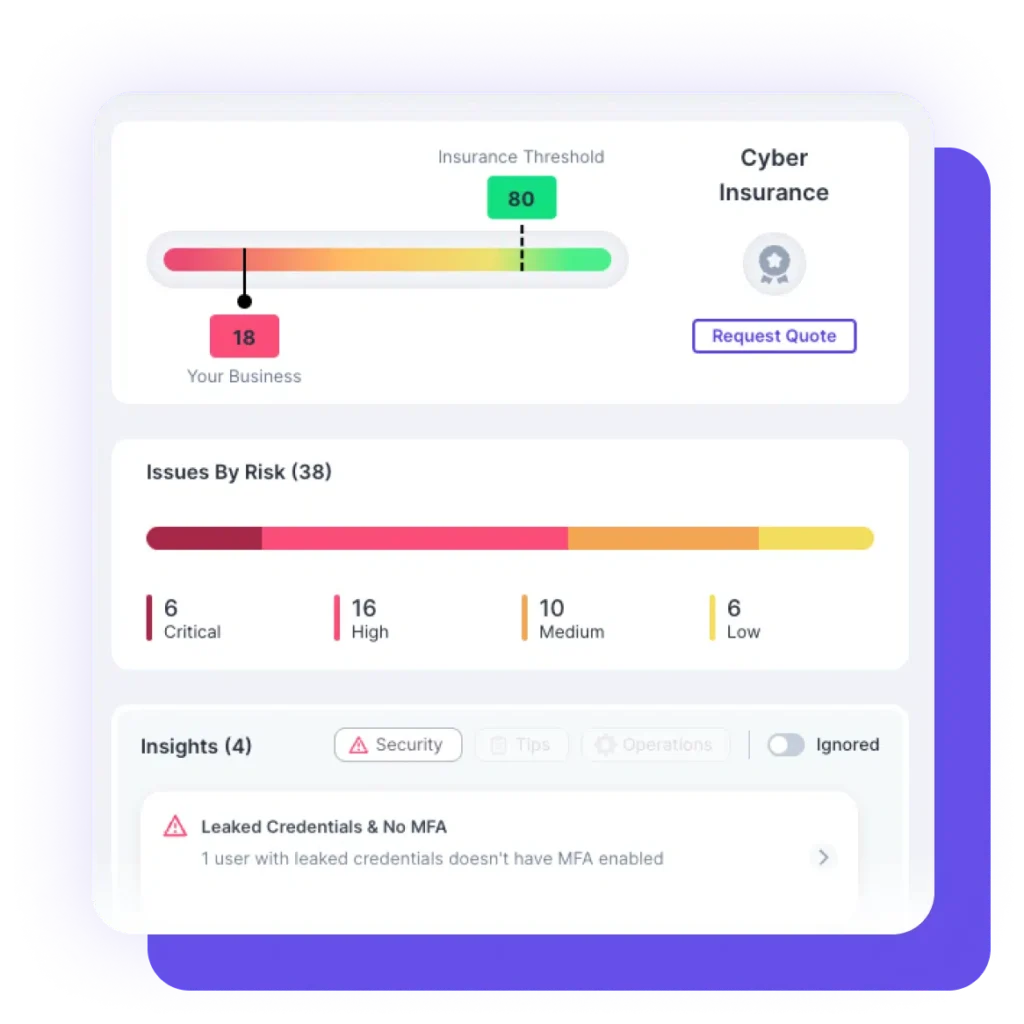
By regularly checking for software updates, reading security news and blogs, and by adopting solutions like CTS Cyber Threat Security that will alert you if any threat arises.
No, there are currently no limits on number of devices or number of organizations supported in the CTS Cyber Threat Security control dashboard.
CTS Cyber Threat Security admins can distribute the device agent via RMM tools in an automated fashion or send emails for users to manually download and install on their computers
CTS Cyber Threat Security supports Windows and Mac devices.

