Stay ahead of potential email threats by utilizing a user-friendly and comprehensive API-based email security solution.





With an innovative solution and multi-layered approach, CTS Cyber Threat Security ensures that email security is always up-to-date, protected against the latest threats, and insured to mitigate financial risk in the case of a breach.
With CTS Cyber Threat Security, employee or client inboxes are secured with advanced anti-phishing email protection solution, along with high-end cyber technology accessible to all businesses.
Email is widely used in business communication because of its organizational benefits, accessibility, authenticity, and privacy advantages. Nonetheless, its popularity also makes it an appealing target for cyber criminals.
Hackers use phishing to trick people into giving away sensitive information, such as passwords or credit card details, by posing as a trustworthy entity or person.
Hackers use this targeted form of phishing to gather information about businesses to draft personalized and convincing messages that are more likely to succeed.
Unsolicited and unwanted messages, often sent in bulk, that can include advertisements, scams, or malware.
Social engineering involves manipulating people into revealing confidential information. It exploits human trust to gain unauthorized access to data or systems.
Malware is any program or code designed to harm or exploit computer systems, including viruses, worms, Trojans, and other types of malicious software.
Did you know 91% of phishing attacks begin with a malicious email?
Did you know 91% of phishing attacks begin with a malicious email?
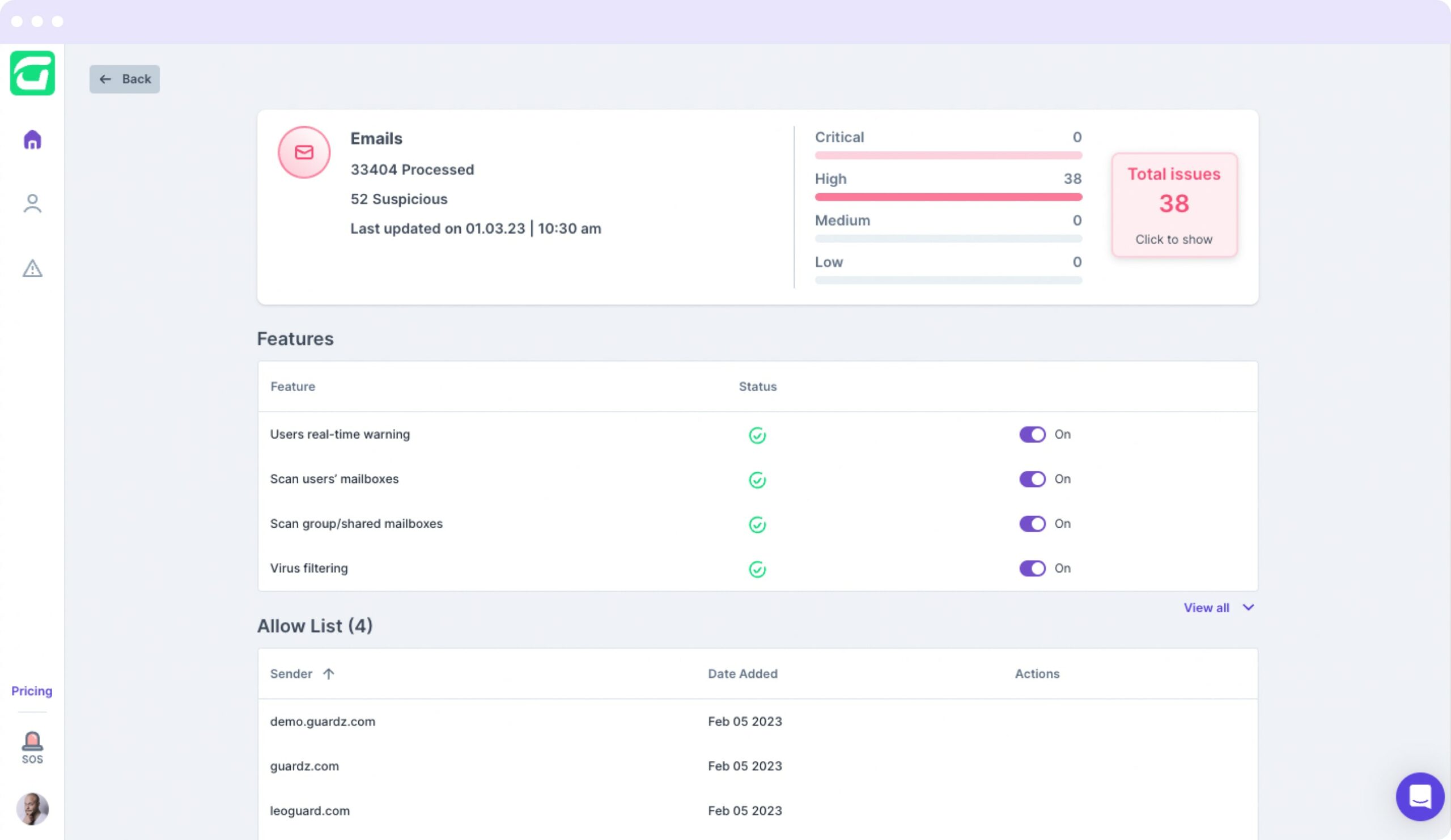
CTS Cyber Threat Security is a fully managed cloud-based solution, meaning that you no longer have to take care of the setup, installation, and configuration of the email protection software. This enables you to leverage the cloud to adapt to your business’s ever-changing needs or manage your clients’ environments at scale.
By leveraging the power of APIs, CTS Cyber Threat Security streamlines the process of email scanning and seamlessly integrates with your existing Microsoft 365 and Google Workspace accounts, providing an additional layer of protection to safeguard your business or clients from potential cybersecurity threats lurking in your incoming emails.
CTS Cyber Threat Security identifies suspicious patterns by analyzing email headers and other metadata. This enables us to alert you about potential malicious emails before they can cause any damage. We stay ahead of the game by aggregating user feedback across a global set of intelligence tools.
CTS Cyber Threat Security utilizes external databases to identify malicious emails and anti-virus software to detect viruses that may appear in email attachments, providing comprehensive protection for all attack vectors. We also regularly update our databases and anti-virus software to stay current with new threats.
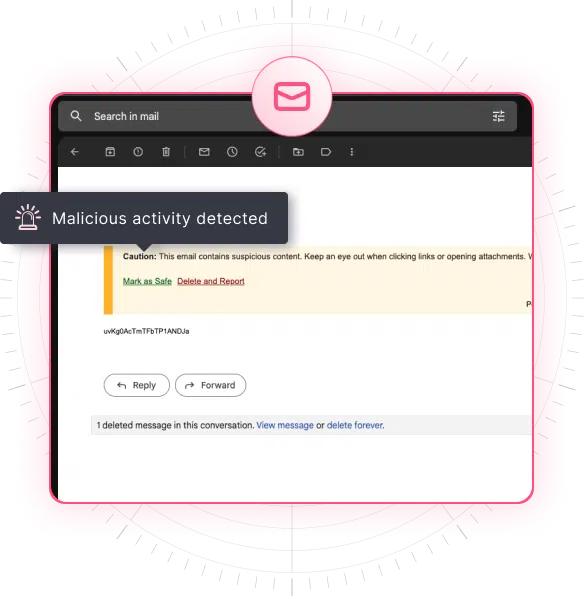
If a potentially harmful email is detected, CTS Cyber Threat Security immediately injects warnings on the email and recommends actions that should be taken. This enables employees and clients to take direct action, deleting the email or collaborating with the security team, to prevent damage or propagation of the threat.
Remove malicious emails once they have reached your employees’ or clients’ inboxes. With this capability, you can be assured that any suspicious emails will be automatically flagged and removed from their inboxes by the IT admin, preventing potential damage to your business.
CTS continuously scans for all inbound traffic and initiates detection through our anti-phishing and anti-malware engines powered by AI.
CTS will then send an alert to inform the IT admin of the threat.
The CTS auto-remediation tool deletes the email or allows them to be marked as safe. When an email is safe, the domain may be added to an allow list to avoid future alerts.
We educate users and prepare them for future threats, we send an awareness campaign to all infected users and provide training as dictated by company program manager or owner.


Centrally navigate the security of multiple clients, each with their unique environments and potential attack vectors, from a single platform, ensuring efficiency, better visibility, and consistency when securing your clients’ systems and data.
With one-click remediation and powerful integrations, even non-security experts can swiftly respond to cyber events.
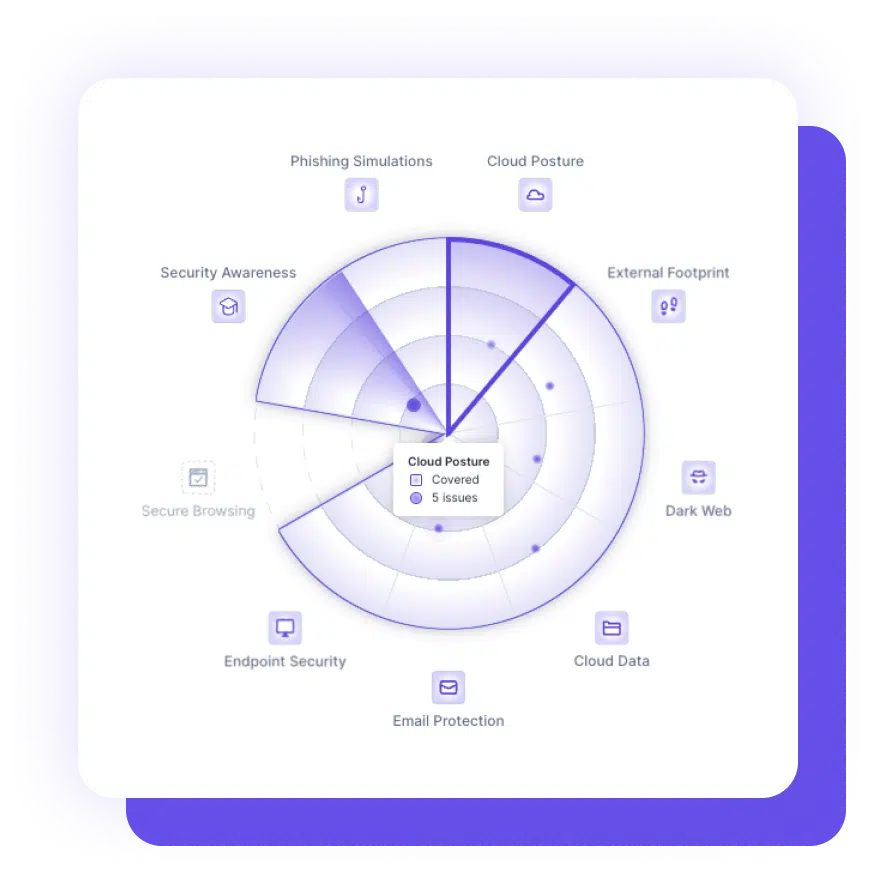


Email protection is a measure to secure email communication from unauthorized access and malicious attacks. It includes protecting against spam, phishing, malware, and other cyber threats.
A secure email gateway is an email security solution that sits between an organization’s email infrastructure and the internet. It scans incoming and outgoing emails for spam, viruses, malware, and other threats. A secure email gateway can also provide encryption and archiving capabilities. There is also an API-based capability (Application Programming Interfaces) that integrates security features into email platforms which scan email attachments and links, block spam and phishing attempts, and detect malware and ransomware. CTS Cyber Threat Security all-in-one cyber security solution provides 24/7 protection against cyber threats so you can have the confidence to focus on building your business.
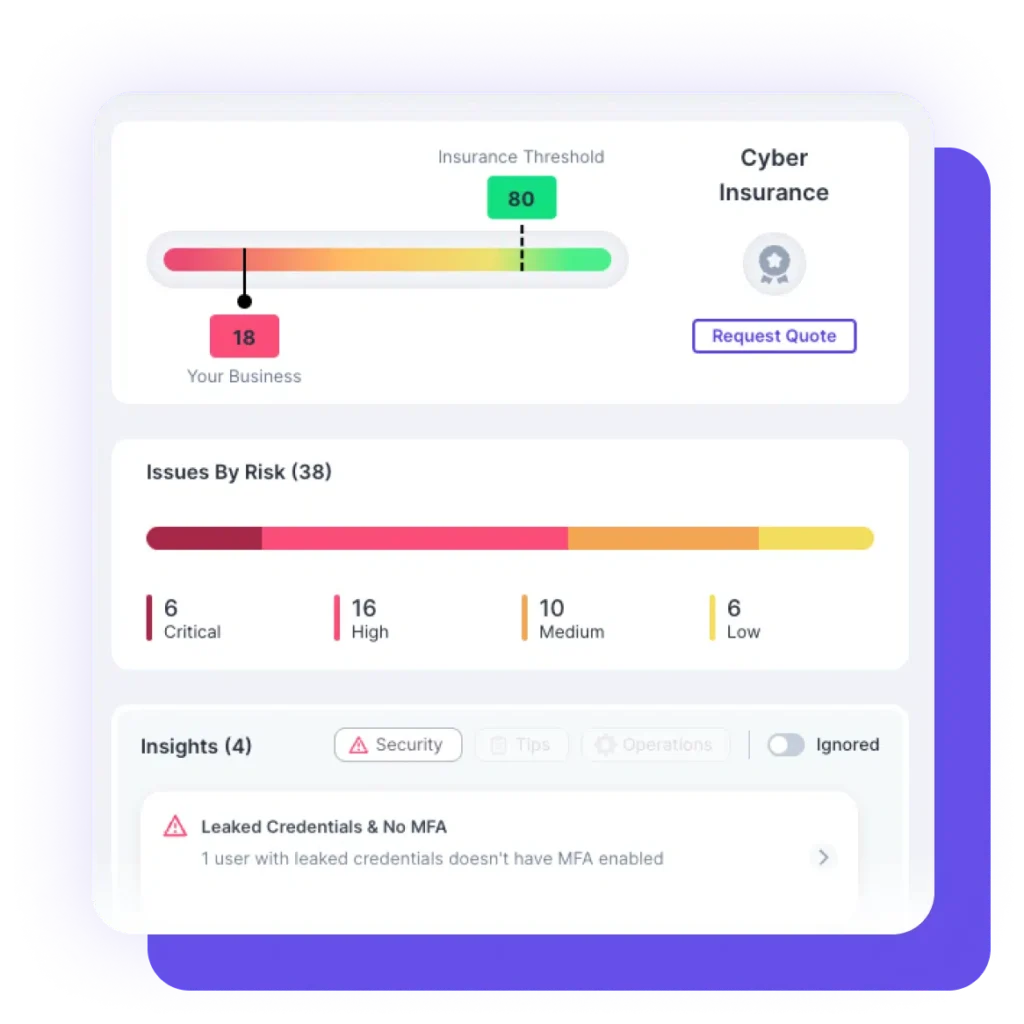
Small business email security is critical to risk management due to the high risk of email-based attacks. According to the Ponemon Institute, the average cost of a data breach caused by a compromised email account was $4.9 million. Implementing strong security measures and educating employees on best practices can help mitigate risks, protect sensitive information, and maintain customer trust.
Regular email is a significant security risk, as cybercriminals can intercept emails and access sensitive information, while human error can also lead to data breaches. Secure email offers additional protection against cyber threats through encryption, anti-spam and anti-virus software, and authentication. It also allows for the implementation of policies and controls to reduce the risk of human error and ensure secure handling of sensitive data, ultimately reducing the risk of data breaches and cyber attacks.
While having access to a secure solution is important, it is equally essential to use it correctly. Ensuring compliance with regulations, promoting user-friendliness, and raising awareness among users are all critical in achieving the full benefits of a secure solution. The CTS Cyber Threat Security intuitive interface enables users to navigate through the platform with ease, as well as provides 24/7 support if for any reason the user has any questions.
While email protection measures can significantly reduce the risk of email threats, it is impossible to prevent all threats. Therefore, it is important to remain vigilant and report any suspicious emails to IT or security personnel.

