CTS Cyber Threat Security connects to data in the cloud and secures several vectors of attack while exposing the risks of intentional and accidental data exfiltration.


Unauthorized access to confidential company data end systems can occur in the cloud due to weak security measures, poor configurations, or lack of MFA.
The ease of cloud collaboration also increases the likelihood of data-at-rest exposure through intentional or unintentional data sharing.
Granting cloud access permissions often disregard the principles of least privilege, resulting in excessive authority and increased risk regarding the sovereignty and potential destruction of data.
Ransomware or other malware running on a device often has the intent of data exfiltration for criminal purposes. Sometimes this malware will execute immediately, while other times, it will lay at rest or behave as an advanced persistent threat (APT).
Increase in ransomware attacks occurred in 2023
Of ransomware attacks target small businesses
Estimated global ransomware damages projected to exceed by 2023
CTS Cyber Threat Security continuously monitors the dark web for leaked credentials and signs of exfiltrated data, which could lead to a targeted BEC attack.
Employees are the first line of defense, so training them to recognize and detect indicators of data theft fosters a culture of caution and vigilance while developing best practices around data security.
CTS scans customer cloud environments for digital assets with excessive sharing permissions and abnormal activity.

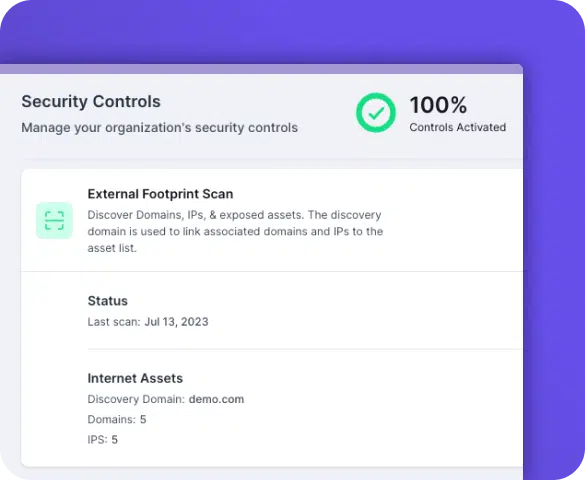
CTS Cyber Threat Security external risk monitoring offers an essential component to protect against ransomware attacks by conducting an automatic external surface scan. By assessing a business’s digital footprint, the solution identifies exposed services, and vulnerable software.
CTS Cyber Threat Security ensures that employees’ and clients’ digital assets remain secure from targeted malware attacks that take advantage of external vulnerabilities while preventing known CVEs are key vectors for cybercriminal exploitation.
CTS Cyber Threat Security ensures up-to-date employee training by notifying admins of training status and recommending industry-standard best practices. Customizable campaign planning allows businesses to target specific users and meet company goals.
Phishing simulations help employees learn to avoid threats like ransomware and malware, while mandatory evaluations measure the impact of training.

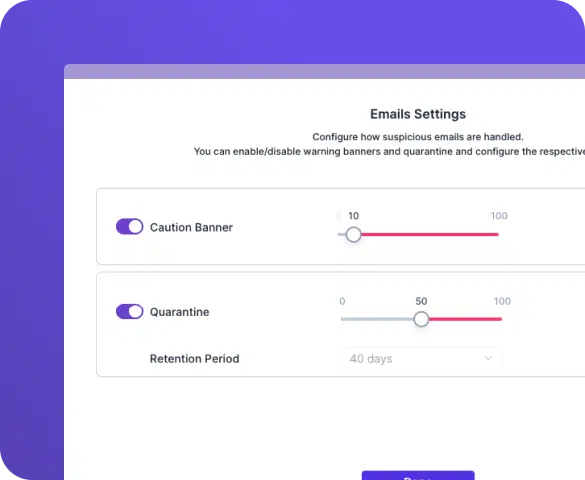
CTS Cyber Threat Security streamlines email protection with its fully managed, cloud-based solution that eliminates manual setup and seamlessly integrates with Microsoft 365 and Google Workspace accounts. Leveraging advanced predictive analysis, global intelligence tools, and continuous updates, Guardz provides robust defense against multiple attack vectors.
High-risk emails are immediately placed into quarantine to programmatically remove the threat. Employees receive warnings and recommended actions for potentially harmful emails, while IT admins can automatically flag and remove malicious messages.
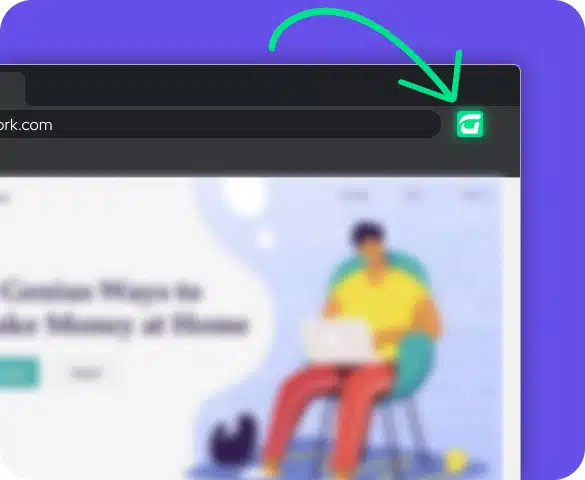
CTS Cyber Threat Security browser extension plays a vital role in safeguarding employees’ online security as they engage in their daily internet activities. Working seamlessly with the main platform, the extension actively monitors access to known malicious websites, web redirects to phishing sites, and continuously scans for unsafe browser extensions.
By offering real-time alerts and comprehensive website analysis, the CTS Cyber Threat Security browser extension empowers employees to make informed decisions and navigate the internet safely.
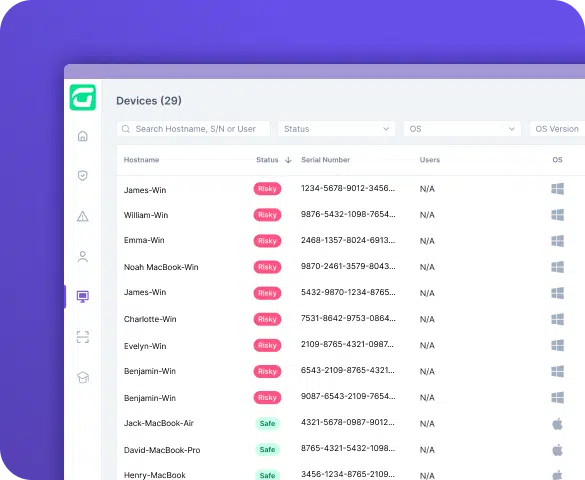
CTS Cyber Threat Security provides an instrumental layer of security by pairing with Microsoft Defender Antivirus to proactively manage endpoint security for your organization. Performing ongoing scans in real-time on each device, the solution uncovers potential gaps in security posture, alignment with Defender policy settings and detection of real-world threats.
Strengthening internal security, CTS Cyber Threat Security assures your organization’s digital assets are protected against targeted digital attacks that exploit internal weaknesses. CTS Cyber Threat Security not only identifies these threats but provides real-time responses, including automated remediations, generating playbooks to address any issues, as well as offering a valuable snapshot of all processes for thorough investigation and research.
Some common signs are an unexpected screen alert or pop-up message indication that your data has been encrypted, demands for a ransom payment in exchange for a decryption key, inability to access your files, and your system working slower than usual.
If you become a victim of a ransomware attack, it is advised not to pay the ransom. Instead, disconnect the affected device from your network to prevent the ransomware from spreading. Report the attack to the local authorities and get professional help to remove the ransomware. If possible, restore your files from a clean backup.
Paying the ransom doesn’t guarantee you will get your files back. It also pushes the cybercriminals to target more people and makes this kind of illegal activity attractive to others. Rather seek proffessional help before taking next steps.
Ransomware attacks can be prevented by regularly updating and patching systems, using reliable, and holisitic security solutions like CTS Cyber Threat Security, backing up important data, avoiding suspicious emails and links, and educating employees or users about the dangers of phishing scams.
Antivirus programs can detect and remove many types of malware, including some ransomware strains. However, no solution is 100% effective, so practicing safe browsing habits and regular data backups is also crucial.
The recovery time can vary widely depending on the extent of the attack and the availability of up-to-date backups. It can range from a few hours to several days or even weeks.

