Streamline cloud data protection and permission visibility to reduce the risks of intentional or accidental data exposure.



With an innovative solution and multi-layered approach, CTS Cyber Threat Security ensures that cloud data are always up-to-date, protected against the latest cyber threats, and insured to mitigate the financial risk in the case of a breach.
Rest assured that employee and clients’ cloud apps are secured with high-end cyber technology accessible to all businesses.

Risky configurations in essential cloud apps can reduce the cloud security posture and lead to avoidable breaches.
80% of companies have experienced
at least one cloud security incident in the last year
CTS Cyber Threat Security manages access to files and folders using best security practices. If confidential data is shared or made public, an alert is sent to the IT admin.
CTS Cyber Threat Security generates alerts in the platform after scanning org-wide Multi-Factor Authentication (MFA) enforcement as well as checking individual user compliance.
CTS Cyber Threat Security scans the current authentication, access and data control settings and analyzes the SaaS posture to recommend areas of improvement.
CTS Cyber Threat Security applies machine learning capabilities to reduce targeted hacks and insider threats typically seen via failed logins, geo-location, and anomalous user behaviors.
CTS Cyber Threat Security detects third-party apps used by employees or clients and scans Google and Microsoft accounts for excessive permissions granted to these apps, revoking them via API.
Programmatically resolve cloud app issues by forcing secure authentication, suspending users, and modifying sharing permissions, while enhancing productivity.





When it comes to managing multiple clients, it can be overwhelming to address every potential threat. CTS Cyber Threat Security enables you to seamlessly oversee and navigate your portfolio of clients’ threats from the start, saving you time.
Centrally navigate the security of multiple clients, each with their unique environments and potential attack vectors, from a single platform, ensuring efficiency, better visibility, and consistency when securing your clients’ systems and data.
With one-click remediation and powerful integrations, even non-security experts can swiftly respond to cyber events.
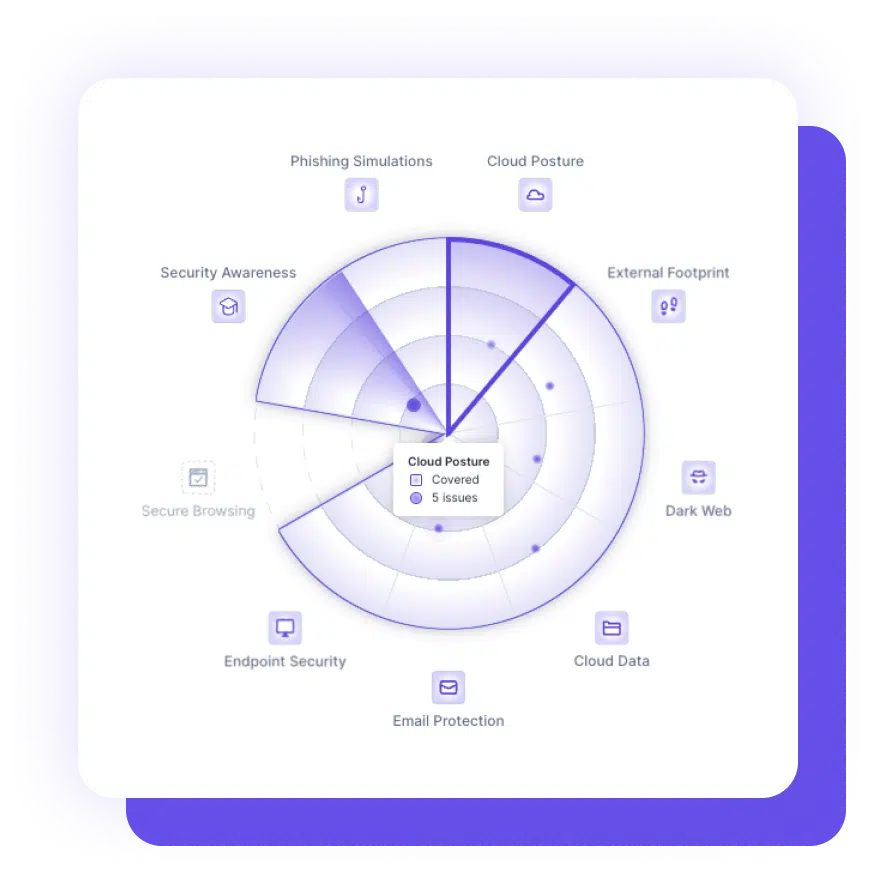


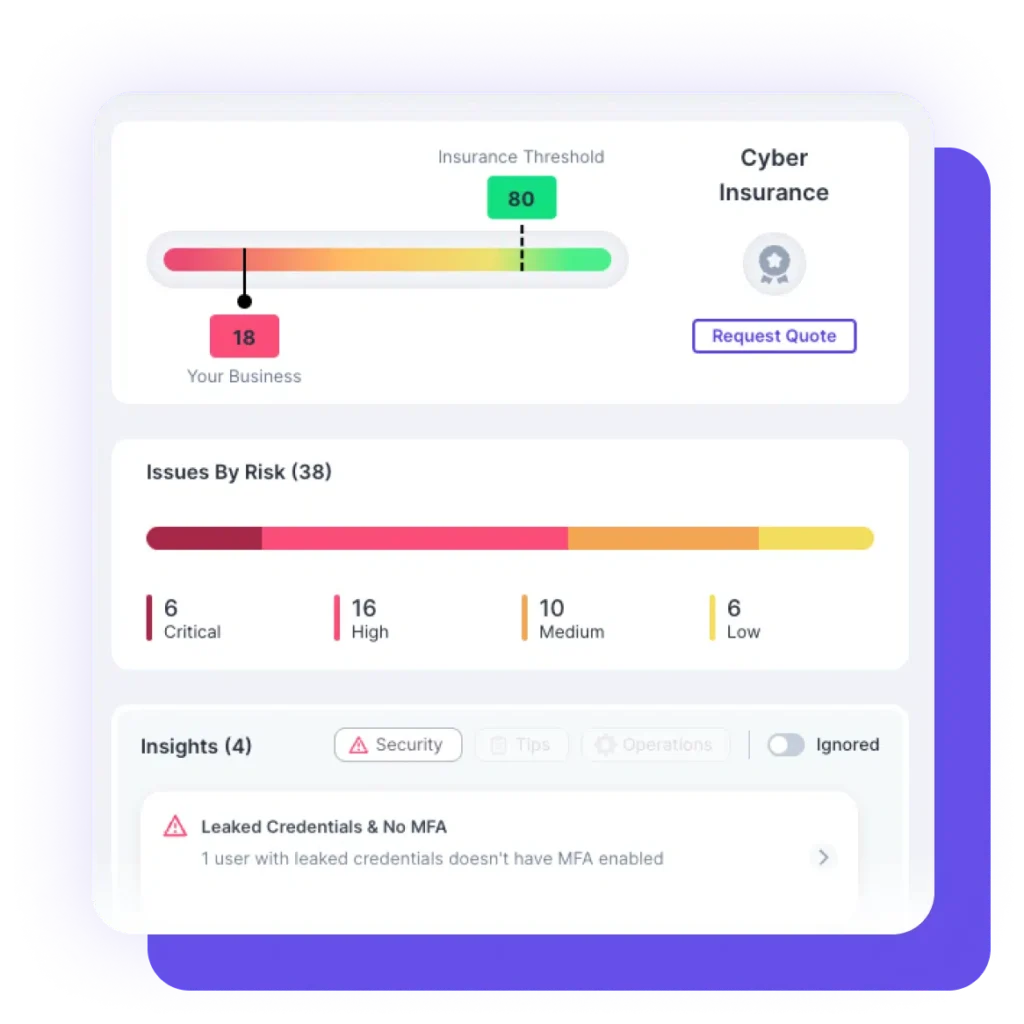
Cloud Data Protection works by analyzing user activity and behavior within cloud applications to identify and prevent threats. It uses machine learning algorithms to detect anomalies and potential security risks, and can apply policies and controls to protect data and resources.
As more organizations adopt cloud-based solutions, it becomes increasingly important to secure these solutions from cyber threats and attacks. Cloud App Security provides features such as data encryption, access control, and threat detection to ensure that cloud-based data and applications are protected from unauthorized access and cyber threats.
If developed and implemented properly, cloud applications can be trusted to keep your data safe. Therefore, it is essential to choose a reputable cloud provider and use security applications that are regularly updated and maintained to ensure the highest level of security.

